Information Security
In accordance with our Information Security Declaration, we implement measures to maintain the confidentiality, integrity, and availability of information assets, strive to protect our information assets, and aim to enhance the sophistication of our information security management.
Response to Cybersecurity
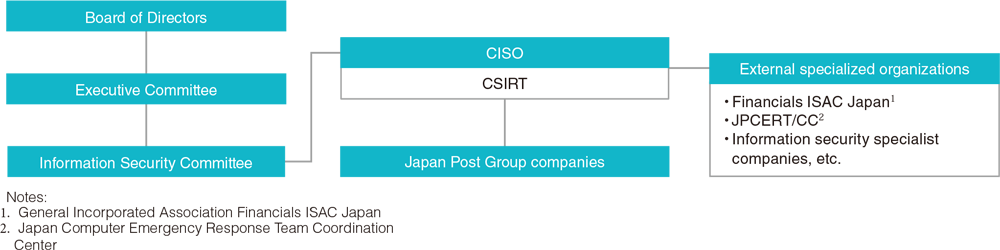
Recognizing the risk of cyberattack as a material risk, we has designated the Chief Compliance Officer as its Chief Information Security Officer (CISO), and implement multi-layered risk management that combines mechanisms to defend and detect unauthorized access and malware under the leadership of our CISO.
Management System
We have established specialized organizations for cybersecurity: the Computer Security Incident Response Team (CSIRT) responsible for preventing and responding to cyber incidents, and the Security Operation Center (SOC) that monitors logs from security and network devices to detect and analyze signs of potential cyber incidents. We also gather information in collaboration with external specialized organizations on a daily basis, working to defend against cyberattacks. We have also established a Business Continuity Plan (BCP) to facilitate rapid recovery in the event of a cyber incident and to minimize any impact on our business.
Human Resources Development and Training
To ensure appropriate responses that prevent damage from spreading in the event of a cyber incident, we actively participate in various training programs and exercises hosted by the National Cybersecurity Office and the Financial Services Agency, in addition to conducting regular internal training and drills. We also conduct regular e-learning and targeted email training for all employees, raising awareness of cyberattacks and promoting knowledge of response measures*, thereby continually enhancing our response capabilities.
(*) If a suspected cyberattack occurs, it must be reported to the CSIRT through the Information Protection Officer assigned to each department.
Security Measures
To prevent damage from attacks exploiting vulnerabilities, we strengthen security measures by conducting threat-based penetration tests by external experts in addition to regular vulnerability assessments.
Governance
To carry out these activities, we have established the Information Security Committee within the Company. Management is taking the lead in promoting such measures, while working in cooperation with other companies in the Japan Post Group based on "Japan Post Group Executive Declaration on Cyber Security." The status of reviews and discussions at the Information Security Committee is regularly reported to the Executive Committee. Important matters are reported to the Board of Directors after they have been discussed and decided by the Executive Committee.
The Internal Audit Department conducts internal audits on the information security management system, including cybersecurity, and verifies the status of its design and operation.
Initiatives for Protecting Personal Information
Japan Post Insurance recognizes the importance of information security management called for by society and promotes measures to protect personal information appropriately, pursuant to relevant laws and regulations.
For an internal management structure to ensure safe management of personal data, we have established and announced the fundamental policy for protecting personal information (Japan Post Insurance Privacy Policy)*1, and have also designated a Chief Information Security Officer (CISO)*2, who is in charge of the Company-wide control of information security, and other responsible personnel. In this way, we are protecting and handling personal information in an appropriate manner.
In addition, we have included information on protecting personal information in our compliance rules and manuals. We have also selected information on personal information protection to include in our annual compliance promotion practice plan, and conduct various training sessions in accordance with the plan.
If personal information is leaked, we will take appropriate actions based on our disciplinary rules, etc. We will also take measures to prevent a recurrence.
The Internal Audit Department conducts off-site monitoring to check the status and operations of compliance with the fundamental policy for protecting personal information.
- (*1)
- The Japan Post Insurance Privacy Policy applies to all of the Company's operations, including those of our contractors.
- (*2)
- The Chief Compliance Officer (CCO) acts as the Chief Information Security Officer (CISO).
<Japan Post Group's Initiatives for the Protection and Management of Customer Information>
Under the revised Act on the Protection of Personal Information which was enforced in April 2022, it is provided that leakage of personal data which is highly likely to damage individual rights and interests shall be reported. The number of cases reported in accordance with the said law during FY2024 was thirty-eight.
The breakdown of each fiscal year is shown in the table below.
【Reference Information】Breakdown by fiscal year according to the categories set forth by the Act on the Protection of Personal Information, etc. as classified by the Japan Post Group
| FY2022 | FY2023 | FY2024 | FY2025 (1Q) |
|
|---|---|---|---|---|
| Sensitive personal information: | 20 | 4 | 5 | 1 |
| Subject to property damage if wrongfully handled: | 22 | 19 | 22 | 6 |
| Leakage that may have been caused for wrongful purposes: | 4 | 2 | 5 | 0 |
| Number of individuals listed on personal data exceeds 1,000: | 0 | 2 | 6 | 1 |
| Total | 46 | 27 | 38 | 8 |
*Quoted from the Japan Post Co., Ltd. website